自己有个小博客,偶尔会在上面写一些东西,记录一些折腾的过程,可以方便自己回溯,也希望能够帮到需要的人。
一晃一年就过去了,去年10月份40多块钱买的华为云轻量也快要到期了,于是终于想起了被遗忘的后台,就去瞅了一眼准备迁移事宜,对于正经的服务器,一般是在运维结束后就关闭防火墙的SSH端口,或者使用iptables来避免被扫描到,同时使用密钥来实现无密码登录,以此增强安全性。
但是我懒,这些都没做。
于是,在某次修改完服务器后,就一直裸奔到了现在,直到今天想起来了还有这档事。
查看日志文件
Ubuntu的登陆日志文件在/var/log/auth.log里,可以ls一下,看看都有啥:
ls /var/log/
alternatives.log btmp.1 dpkg.log.4.gz php8.1-fpm.log.1 syslog.1
alternatives.log.1 chrony dpkg.log.5.gz php8.1-fpm.log.10.gz syslog.2.gz
alternatives.log.2.gz cloud-init.log faillog php8.1-fpm.log.11.gz syslog.3.gz
alternatives.log.3.gz cloud-init-output.log installer php8.1-fpm.log.12.gz syslog.4.gz
alternatives.log.4.gz dist-upgrade journal php8.1-fpm.log.2.gz sysstat
alternatives.log.5.gz dmesg kern.log php8.1-fpm.log.3.gz ubuntu-advantage.log
alternatives.log.6.gz dmesg.0 kern.log.1 php8.1-fpm.log.4.gz ubuntu-advantage.log.1
apt dmesg.1.gz kern.log.2.gz php8.1-fpm.log.5.gz ubuntu-advantage.log.2.gz
auth.log dmesg.2.gz kern.log.3.gz php8.1-fpm.log.6.gz ubuntu-advantage.log.3.gz
auth.log.1 dmesg.3.gz kern.log.4.gz php8.1-fpm.log.7.gz ubuntu-advantage.log.4.gz
auth.log.2.gz dmesg.4.gz landscape php8.1-fpm.log.8.gz ubuntu-advantage.log.5.gz
auth.log.3.gz dpkg.log lastlog php8.1-fpm.log.9.gz ubuntu-advantage.log.6.gz
auth.log.4.gz dpkg.log.1 multi-queue-hw.log unattended-upgrades
bootstrap.log dpkg.log.2.gz nginx private wtmp
btmp dpkg.log.3.gz php8.1-fpm.log syslog
可以看到这里有几个auth.log的文件,如果你开启了日志分文件存储的功能的话,这里就会出现多个日志文件,而之前的日志文件则会被压缩,其中最新的登陆日志就在auth.log这个文件里。
我们先把这些日志文件都复制出来:
sudo cp auth.log* ~/ssh
~/ssh$ ls
auth.log auth.log.1 auth.log.2 auth.log.3 auth.log.4我这个是解压过的,如果有gz压缩文件的话,要先解压。
sudo gzip -d 你的文件名解压完成后就和上面一样了。
这时候还有权限问题,你可能无法访问,我们需要修改一下这些文件的权限。
sudo chmod 755 *修改完权限后,就可以进行下一步操作了。
我这几个日志文件,足足有20多兆,记录了几十万条信息......
预处理日志里的信息
先看一下日志里的内容,这个是一段示例:
Aug 4 00:05:06 hecs-100353 sshd[2200309]: Failed password for invalid user sona from 49.234.32.136 port 56548 ssh2
Aug 4 00:05:07 hecs-100353 sshd[2200309]: Received disconnect from 49.234.32.136 port 56548:11: Bye Bye [preauth]
Aug 4 00:05:07 hecs-100353 sshd[2200309]: Disconnected from invalid user sona 49.234.32.136 port 56548 [preauth]
Aug 4 00:06:13 hecs-100353 sshd[2200315]: Connection reset by 49.234.32.136 port 41944 [preauth]
Aug 4 00:06:37 hecs-100353 sshd[2200318]: Connection reset by 92.118.39.133 port 47714 [preauth]
Aug 4 00:07:26 hecs-100353 sshd[2200322]: Connection reset by 49.234.32.136 port 55570 [preauth]
Aug 4 00:08:36 hecs-100353 sshd[2200330]: Connection reset by 49.234.32.136 port 40964 [preauth]
Aug 4 00:09:01 hecs-100353 CRON[2200334]: pam_unix(cron:session): session opened for user root(uid=0) by (uid=0)
Aug 4 00:09:01 hecs-100353 CRON[2200334]: pam_unix(cron:session): session closed for user root
Aug 4 00:09:46 hecs-100353 sshd[2200397]: Connection reset by 49.234.32.136 port 54586 [preauth]
Aug 4 00:10:57 hecs-100353 sshd[2200409]: Connection reset by 49.234.32.136 port 39982 [preauth]
Aug 4 00:12:02 hecs-100353 sshd[2200568]: Invalid user hamid from 49.234.32.136 port 53606
可以看到,当有人尝试登陆时,在服务器内就会留下这行内容。
Failed password for invalid user sona from 49.234.32.136他们的格式是有规律的,那就好办了。可以用grep这个工具来搜索相应的字段并输出为文件。
grep -r "Failed password" >~/你的文本文件.txt打开输出的文本文件,可以看到现在的内容就规整多了
auth.log:Aug 4 01:06:25 hecs-100353 sshd[2200973]: Failed password for root from 175.125.95.234 port 54476 ssh2
auth.log:Aug 4 01:17:48 hecs-100353 sshd[2201094]: Failed password for root from 183.178.182.198 port 13572 ssh2
auth.log:Aug 4 01:28:07 hecs-100353 sshd[2201157]: Failed password for root from 68.183.227.243 port 46200 ssh2
auth.log:Aug 4 01:31:45 hecs-100353 sshd[2201180]: Failed password for root from 117.83.111.131 port 58376 ssh2
auth.log:Aug 4 01:33:00 hecs-100353 sshd[2201190]: Failed password for invalid user temp from 162.14.108.116 port 56438 ssh2
auth.log:Aug 4 01:38:45 hecs-100353 sshd[2201222]: Failed password for root from 117.83.111.131 port 48004 ssh2
auth.log:Aug 4 01:39:56 hecs-100353 sshd[2201299]: Failed password for root from 187.72.83.169 port 60550 ssh2
auth.log:Aug 4 01:40:31 hecs-100353 sshd[2201310]: Failed password for invalid user xzq from 117.83.111.131 port 45956 ssh2
auth.log:Aug 4 01:42:13 hecs-100353 sshd[2201329]: Failed password for invalid user chy from 117.83.111.131 port 43904 ssh2
auth.log:Aug 4 01:42:29 hecs-100353 sshd[2201331]: Failed password for invalid user projetecno from 162.14.108.116 port 42236 ssh2
auth.log:Aug 4 01:43:02 hecs-100353 sshd[2201337]: Failed password for invalid user sakurai from 162.14.108.116 port 42198 ssh2
auth.log:Aug 4 01:44:23 hecs-100353 sshd[2201355]: Failed password for root from 162.14.108.116 port 51558 ssh2
auth.log:Aug 4 01:44:44 hecs-100353 sshd[2201360]: Failed password for root from 117.83.111.131 port 54942 ssh2
auth.log:Aug 4 01:44:47 hecs-100353 sshd[2201362]: Failed password for root from 162.14.108.116 port 54948 ssh2
auth.log:Aug 4 01:45:31 hecs-100353 sshd[2201376]: Failed password for root from 117.83.111.131 port 39800 ssh2
auth.log:Aug 4 01:46:19 hecs-100353 sshd[2201387]: Failed password for invalid user harlan from 117.83.111.131 port 52888 ssh2
auth.log:Aug 4 01:46:39 hecs-100353 sshd[2201391]: Failed password for root from 162.14.108.116 port 53914 ssh2
auth.log:Aug 4 01:47:25 hecs-100353 sshd[2201401]: Failed password for invalid user ubuntu from 92.118.39.133 port 38998 ssh2
auth.log:Aug 4 01:47:34 hecs-100353 sshd[2201404]: Failed password for invalid user baoanbo from 162.14.108.116 port 57284 ssh2
auth.log:Aug 4 01:48:01 hecs-100353 sshd[2201410]: Failed password for invalid user aba from 162.14.108.116 port 47224 ssh2
auth.log:Aug 4 01:48:45 hecs-100353 sshd[2201418]: Failed password for invalid user kevin from 117.83.111.131 port 35690 ssh2
auth.log:Aug 4 01:49:00 hecs-100353 sshd[2201423]: Failed password for root from 162.14.108.116 port 43716 ssh2
auth.log:Aug 4 01:49:30 hecs-100353 sshd[2201427]: Failed password for invalid user abhijit from 162.14.108.116 port 48736 ssh2
auth.log:Aug 4 01:51:07 hecs-100353 sshd[2201450]: Failed password for root from 162.14.108.116 port 46222 ssh2
auth.log:Aug 4 01:51:55 hecs-100353 sshd[2201459]: Failed password for invalid user rchawla from 187.72.83.169 port 43966 ssh2
统计尝试的用户名和IP数量
这里需要用到一个叫做awk的工具。awk 是一种处理文本文件的语言,是一个强大的文本分析工具。awk 通过提供编程语言的功能,如变量、数学运算、字符串处理等,使得对文本文件的分析和操作变得非常灵活和高效。之所以叫 awk 是因为其取了三位创始人 Alfred Aho,Peter Weinberger, 和 Brian Kernighan 的 Family Name 的首字符。
先统计出尝试的IP和用户名
cat 刚才输出的结果.txt | awk '{print $10 "\t" $8}' | sort其中$10和$8分别对应IP和用户名所在的列数,需要你自己根据需要来修改。
统计用户名和IP数
cat 输出的文件 | awk '{print $8}' | sort | uniq -c | sort -bn最终结果如下:
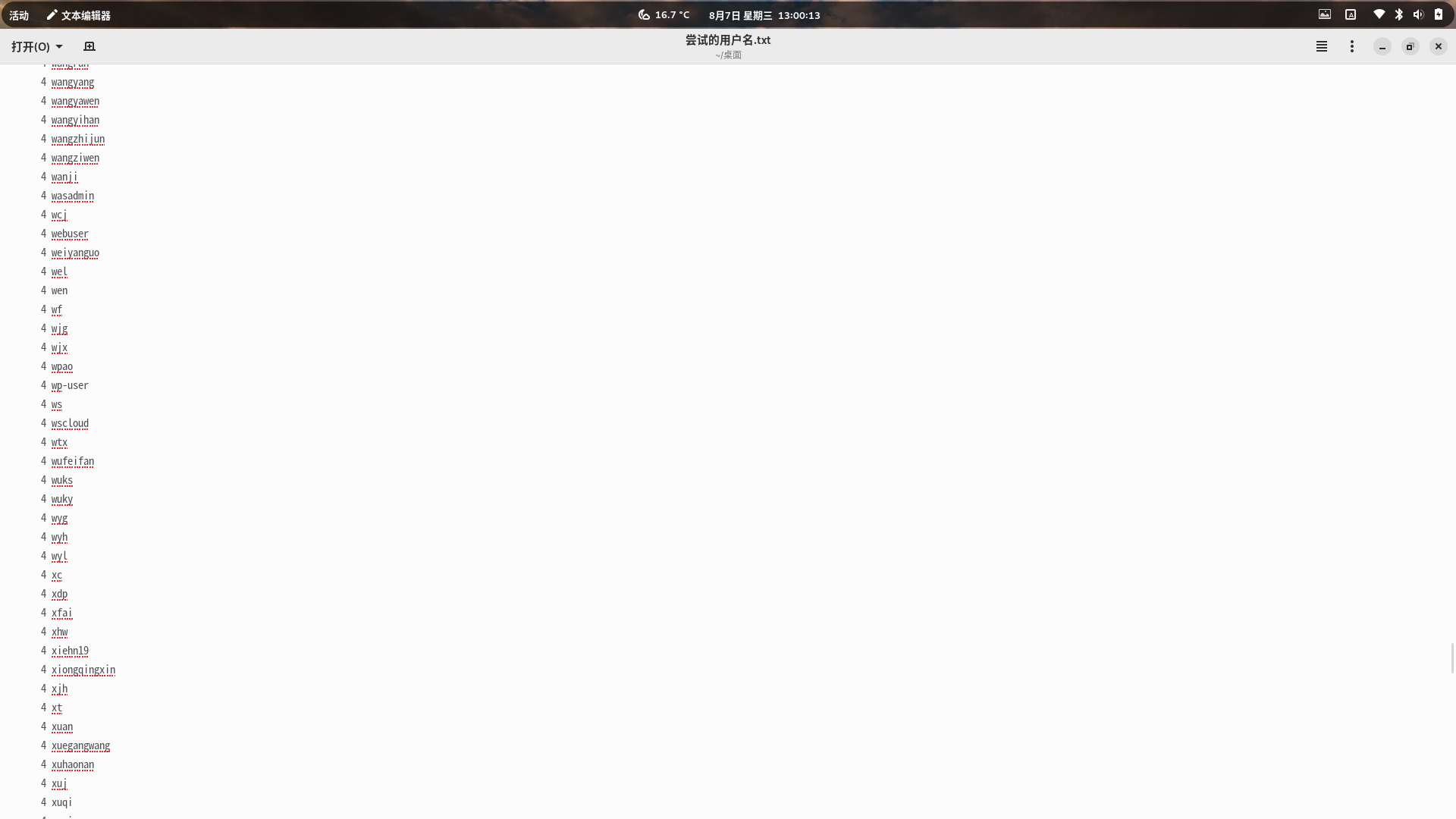
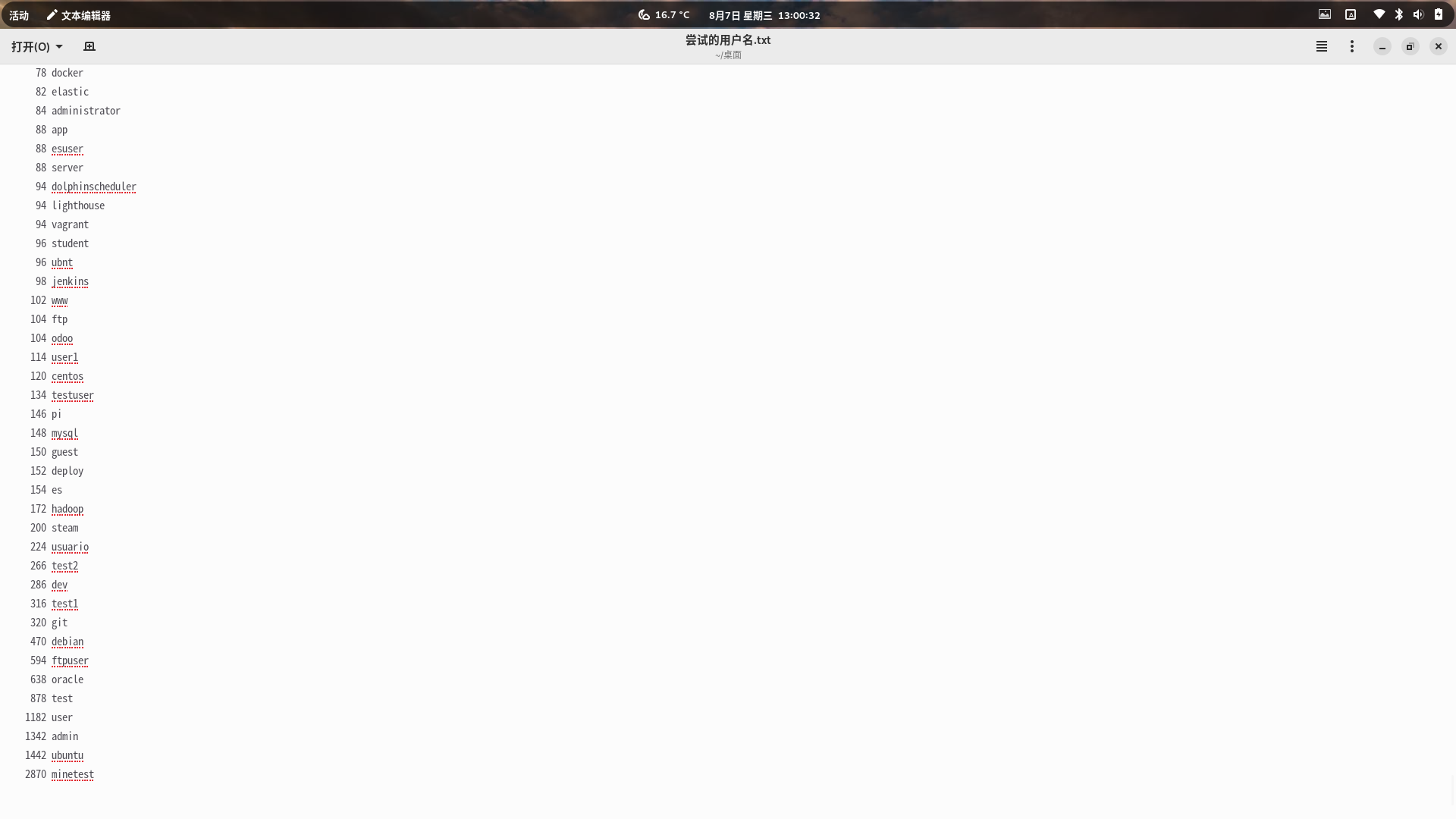
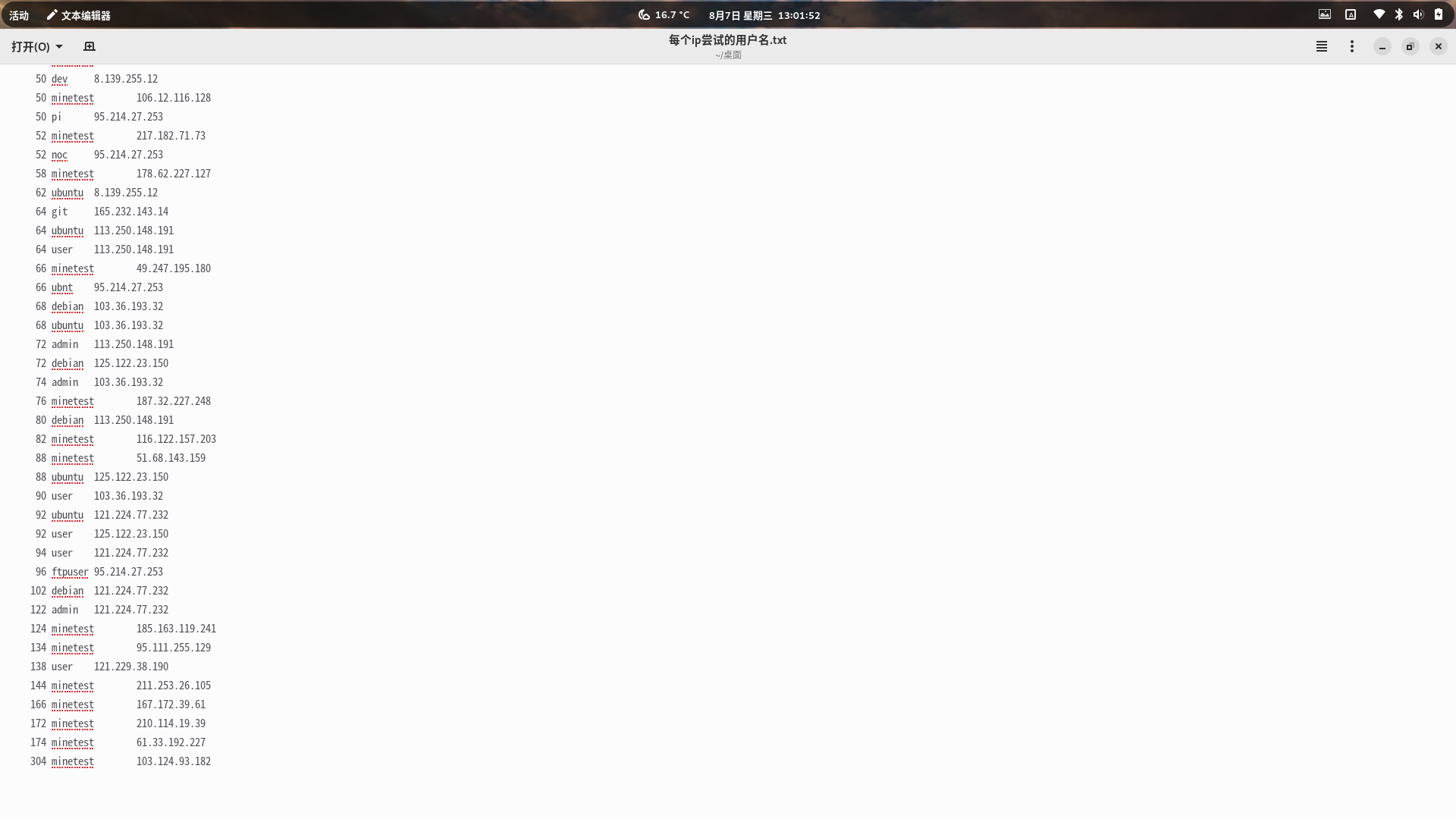
好家伙,这个越南的IP对我网站域名这么执着的吗?
反正过段时间就要迁移了,就这样吧。
